A.I.G (AI-Infra-Guard) is a comprehensive, intelligent, and easy-to-use AI Red Teaming platform developed by Tencent Zhuque Lab.
Documentation
🚀 AI Red Teaming Platform by Tencent Zhuque Lab
A.I.G (AI-Infra-Guard) integrates capabilities such as AI infra vulnerability scan, MCP Server risk scan, and Jailbreak Evaluation, aiming to provide users with the most comprehensive, intelligent, and user-friendly solution for AI security risk self-examination.
We are committed to making A.I.G(AI-Infra-Guard) the industry-leading AI red teaming platform. More stars help this project reach a wider audience, attracting more developers to contribute, which accelerates iteration and improvement. Your star is crucial to us!
📢 News:
* A.I.G v3.5.0 features major improvements in modular architecture, system stability, and detection capabilities. Update now to explore the new version. View all changelog.
* 🎉 A.I.G was featured at Black Hat Arsenal Europe 2025! Check out our presentation slides.
Table of Contents
- 🚀 Quick Start
- ✨ Features
- 🖼️ Showcase
- 📖 User Guide
- 🔧 API Documentation
- 📝 Contribution Guide
- 🙏 Acknowledgements
- 💬 Join the Community
- 📖 Citation
- 📚 Related Papers
- 📄 License
🚀 Quick Start
Deployment with Docker
| Docker | RAM | Disk Space |
|---|---|---|
| 20.10 or higher | 4GB+ | 10GB+ |
# This method pulls pre-built images from Docker Hub for a faster start
git clone https://github.com/Tencent/AI-Infra-Guard.git
cd AI-Infra-Guard
# For Docker Compose V2+, replace 'docker-compose' with 'docker compose'
docker-compose -f docker-compose.images.yml up -dOnce the service is running, you can access the A.I.G web interface at:
http://localhost:8088
📦 More installation options and online pro version
Other Installation Methods
Method 2: One-Click Install Script (Recommended)
# This method will automatically install Docker and launch A.I.G with one command
curl https://raw.githubusercontent.com/Tencent/AI-Infra-Guard/refs/heads/main/docker.sh | bashMethod 3: Build and run from source
git clone https://github.com/Tencent/AI-Infra-Guard.git
cd AI-Infra-Guard
# This method builds a Docker image from local source code and starts the service
# (For Docker Compose V2+, replace 'docker-compose' with 'docker compose')
docker-compose up -dNote: The AI-Infra-Guard project is positioned as an AI red teaming platform for internal use by enterprises or individuals. It currently lacks an authentication mechanism and should not be deployed on public networks.
For more information, see: https://tencent.github.io/AI-Infra-Guard/?menu=getting-started
Try the Online Pro Version
Experience the Pro version with advanced features and improved performance. The Pro version requires an invitation code and is prioritized for contributors who have submitted issues, pull requests, or discussions, or actively help grow the community. Visit: https://aigsec.ai/
✨ Features
| Feature | More Info |
|---|---|
| AI Infra Scan | Precisely identifies over 30 AI framework components and covers over 400 known CVE vulnerabilities, including Ollama, ComfyUI, vLLM, etc. |
| MCP Server Scan | Powered by AI Agent, Detects 9 major categories of MCP security risks, Supports source code/remote URL scanning. |
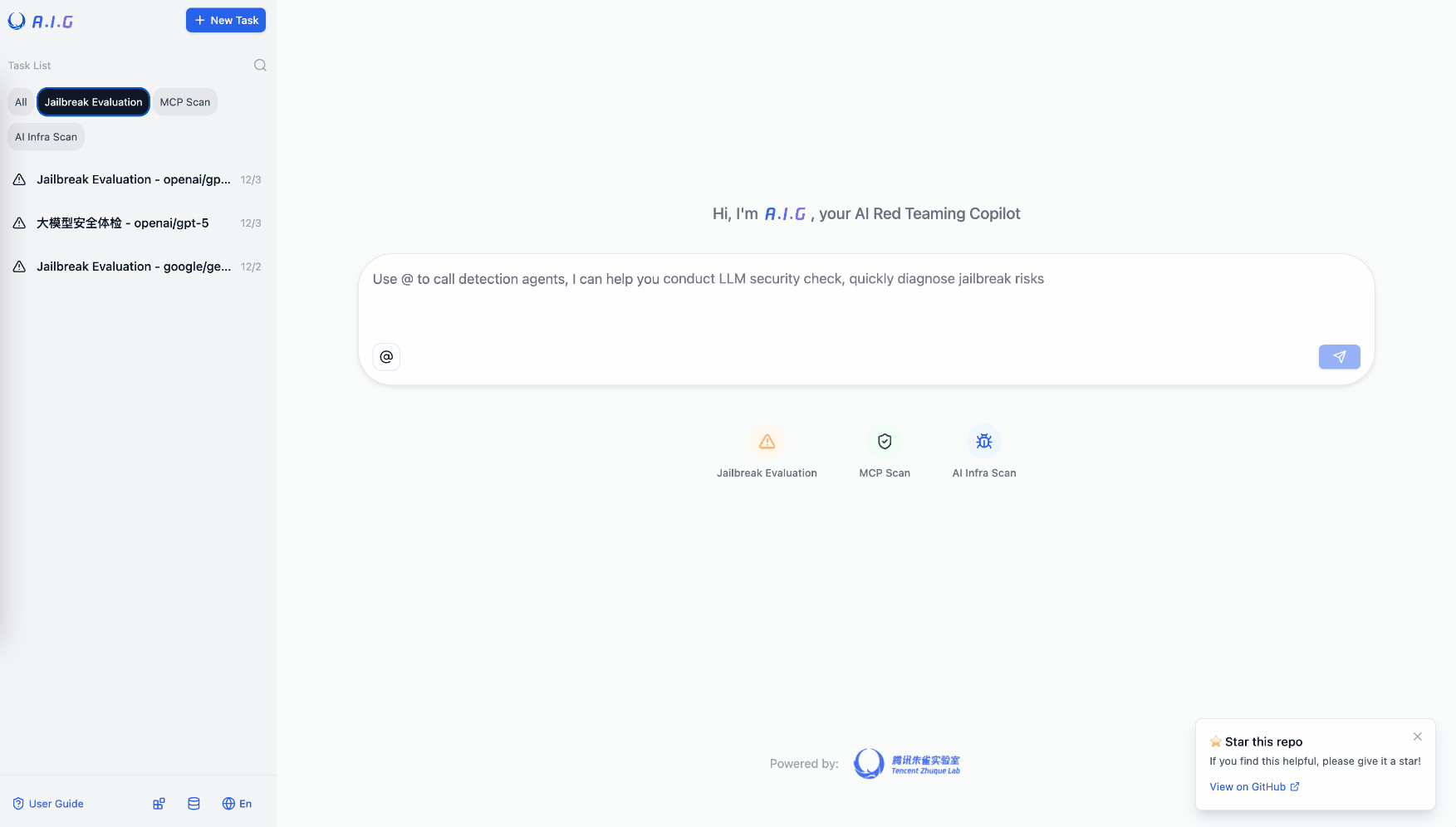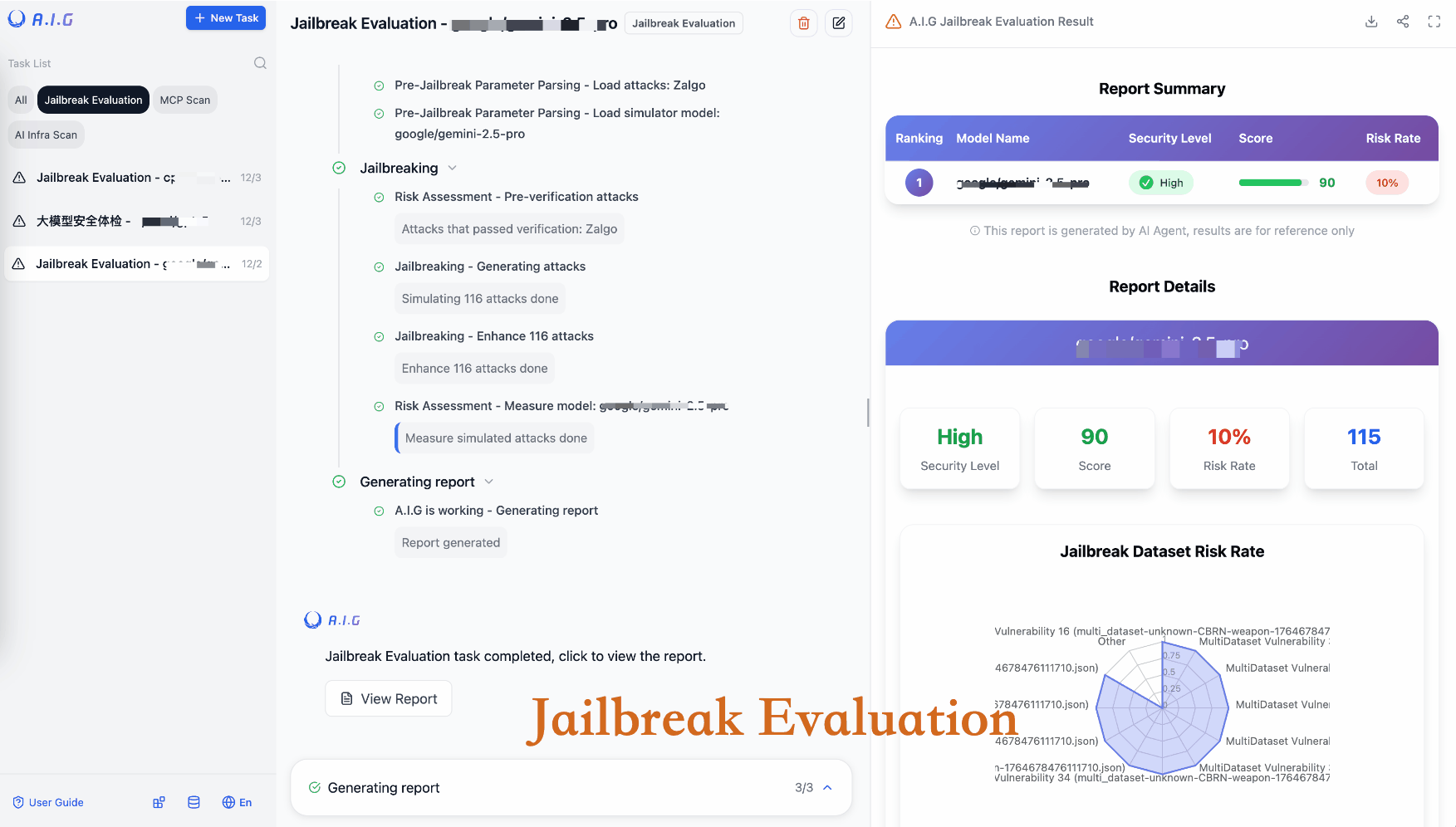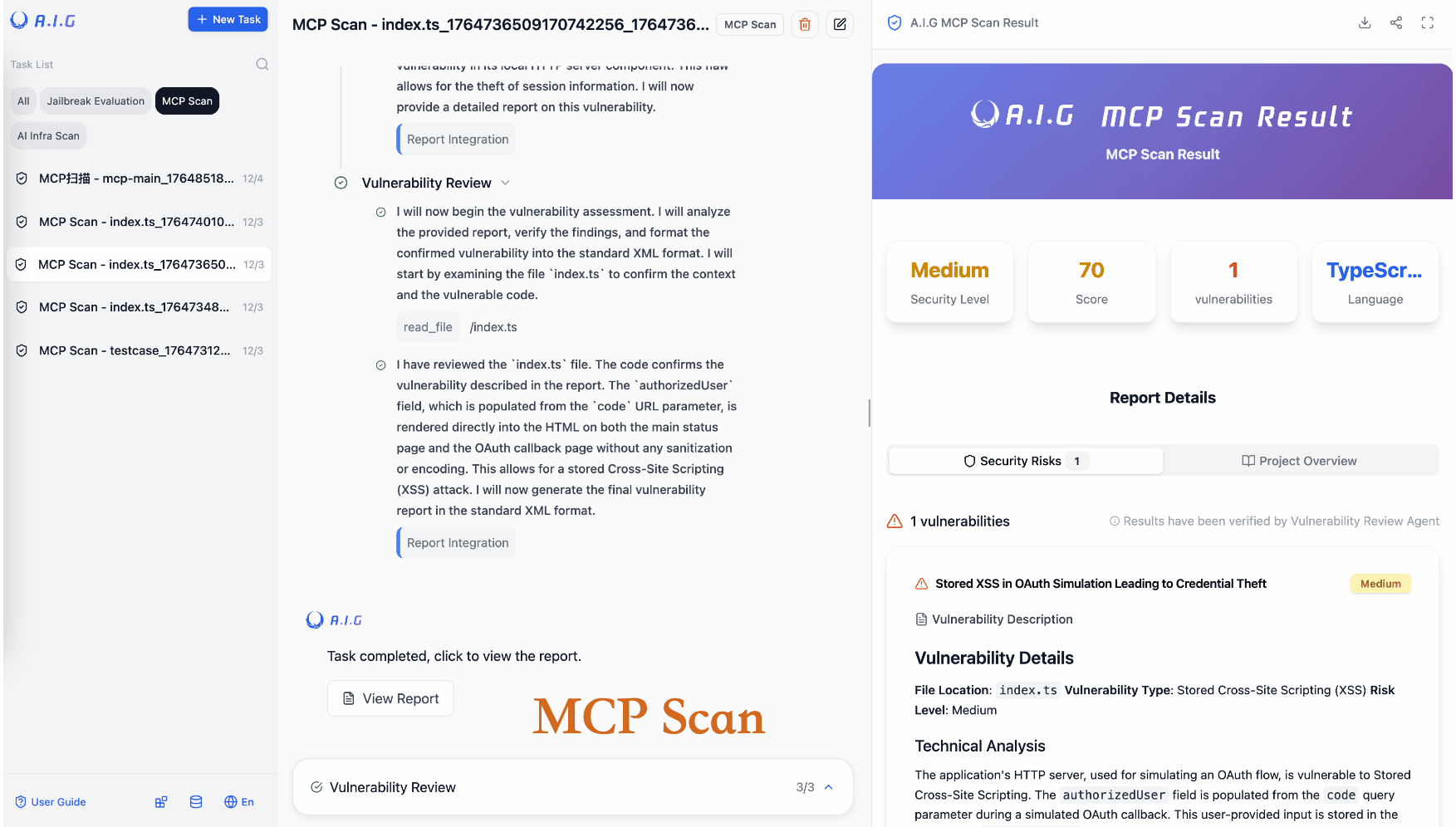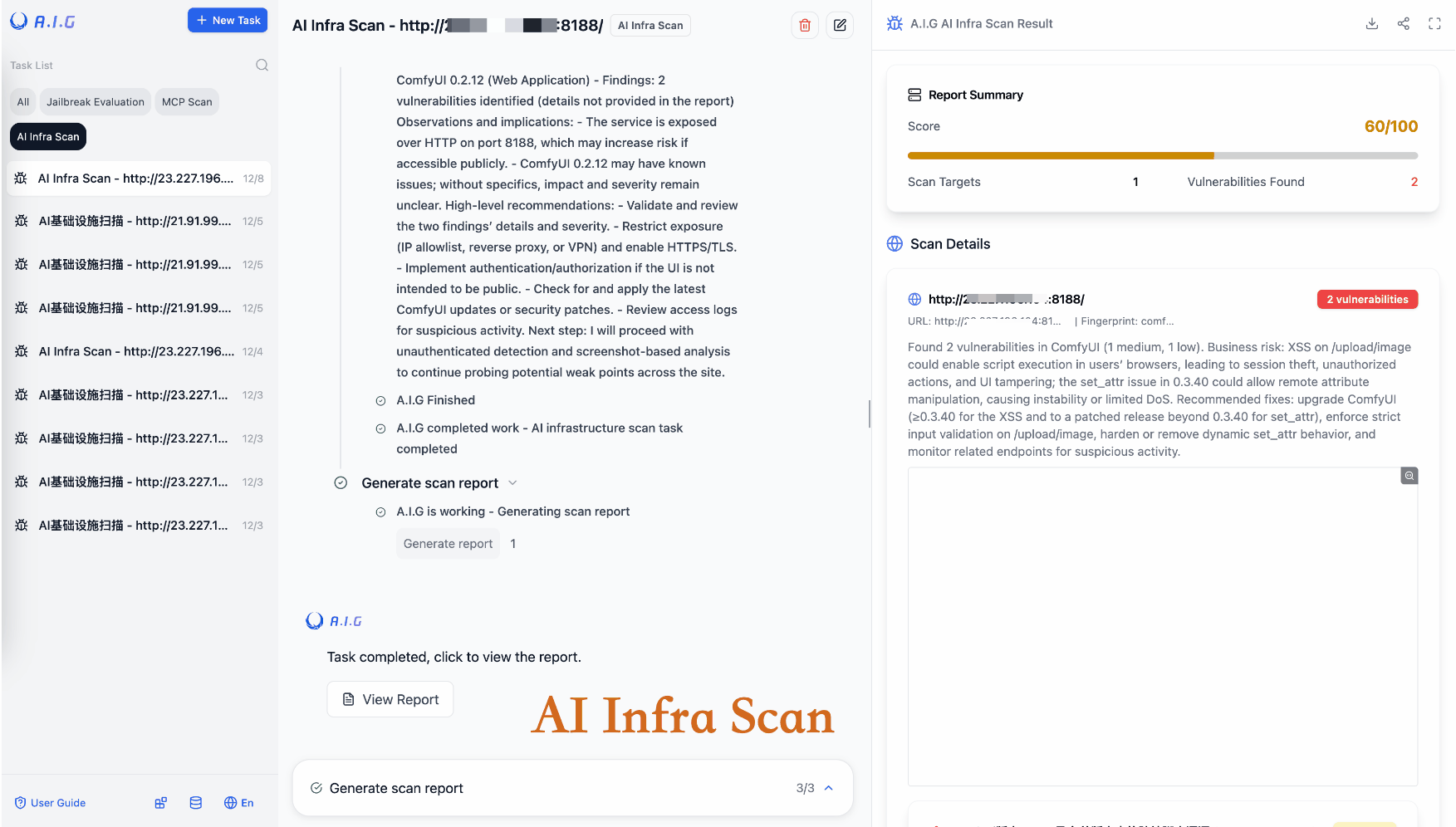
| Jailbreak Evaluation | Assesses prompt security risks with curated datasets and multiple attack methods, Cross-model comparison. |
💎 Additional Benefits
- 🖥️ Modern Web Interface: User-friendly UI with one-click scanning and real-time progress tracking
- 🔌 Complete API: Full interface documentation and Swagger specifications for easy integration
- 🌐 Multi-Language: Chinese and English interfaces with localized documentation
- 🐳 Cross-Platform: Linux, macOS, and Windows support with Docker-based deployment
- 🆓 Free & Open Source: Completely free under the MIT license
🖼️ Showcase
A.I.G Main Interface
Plugin Management
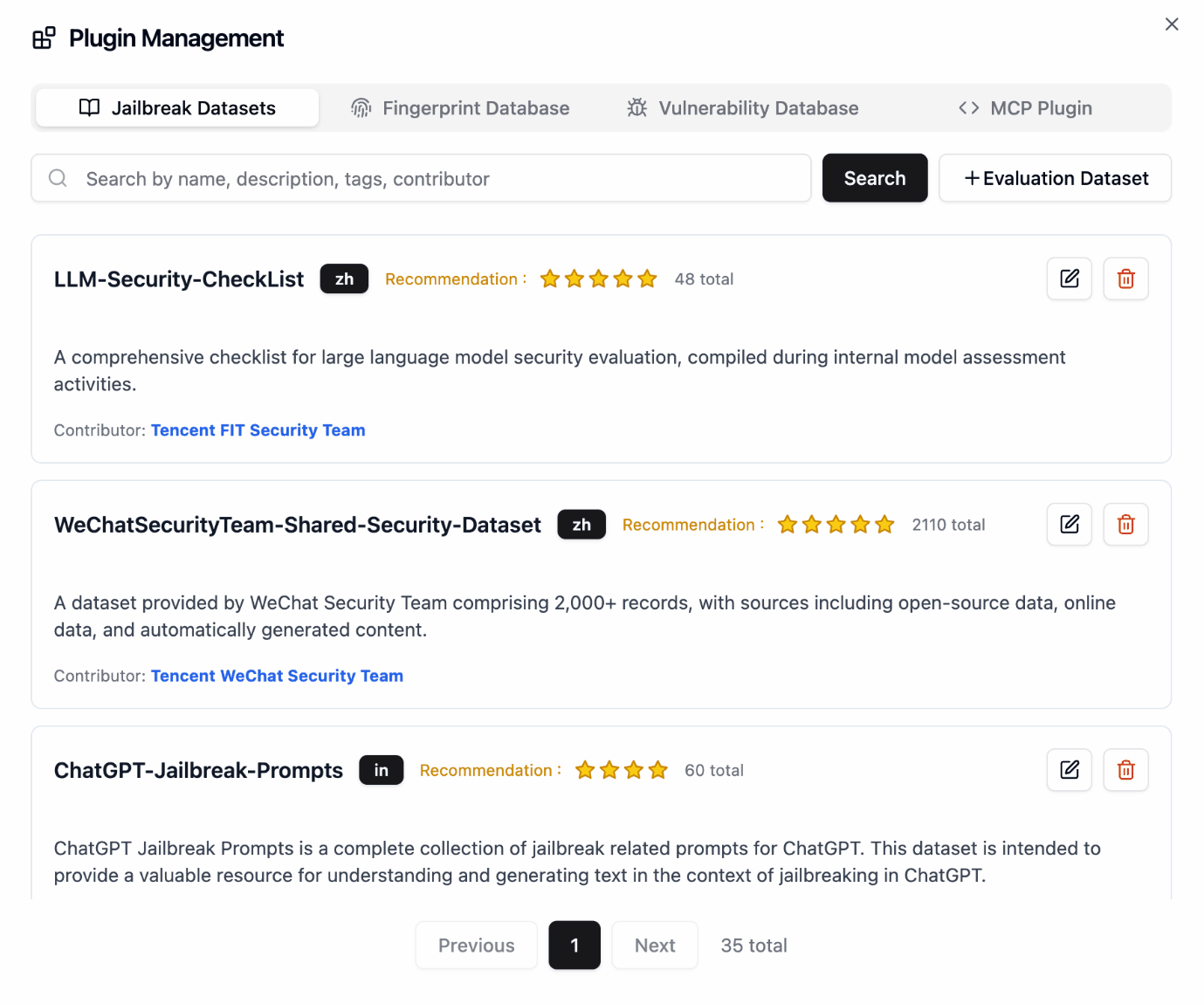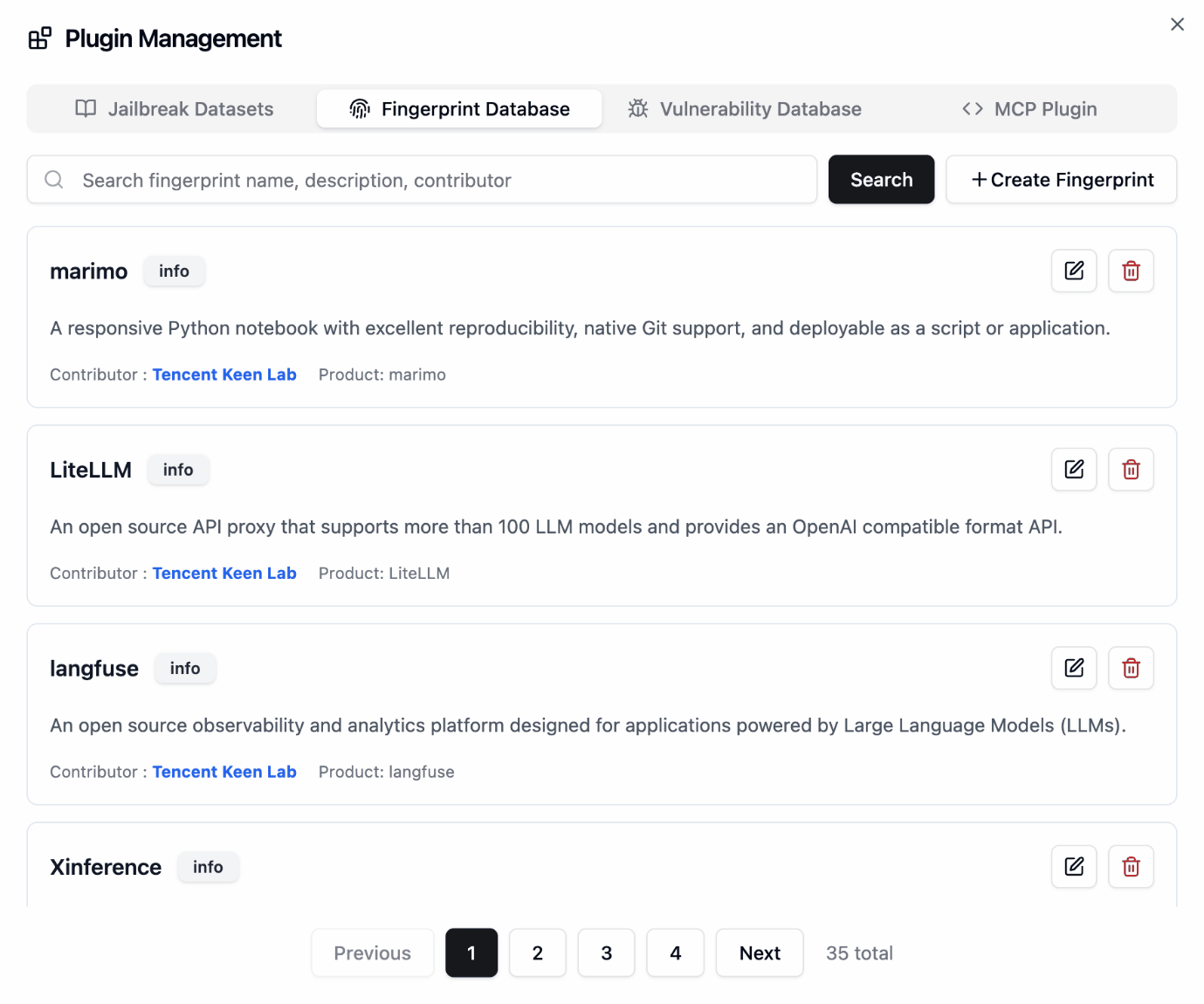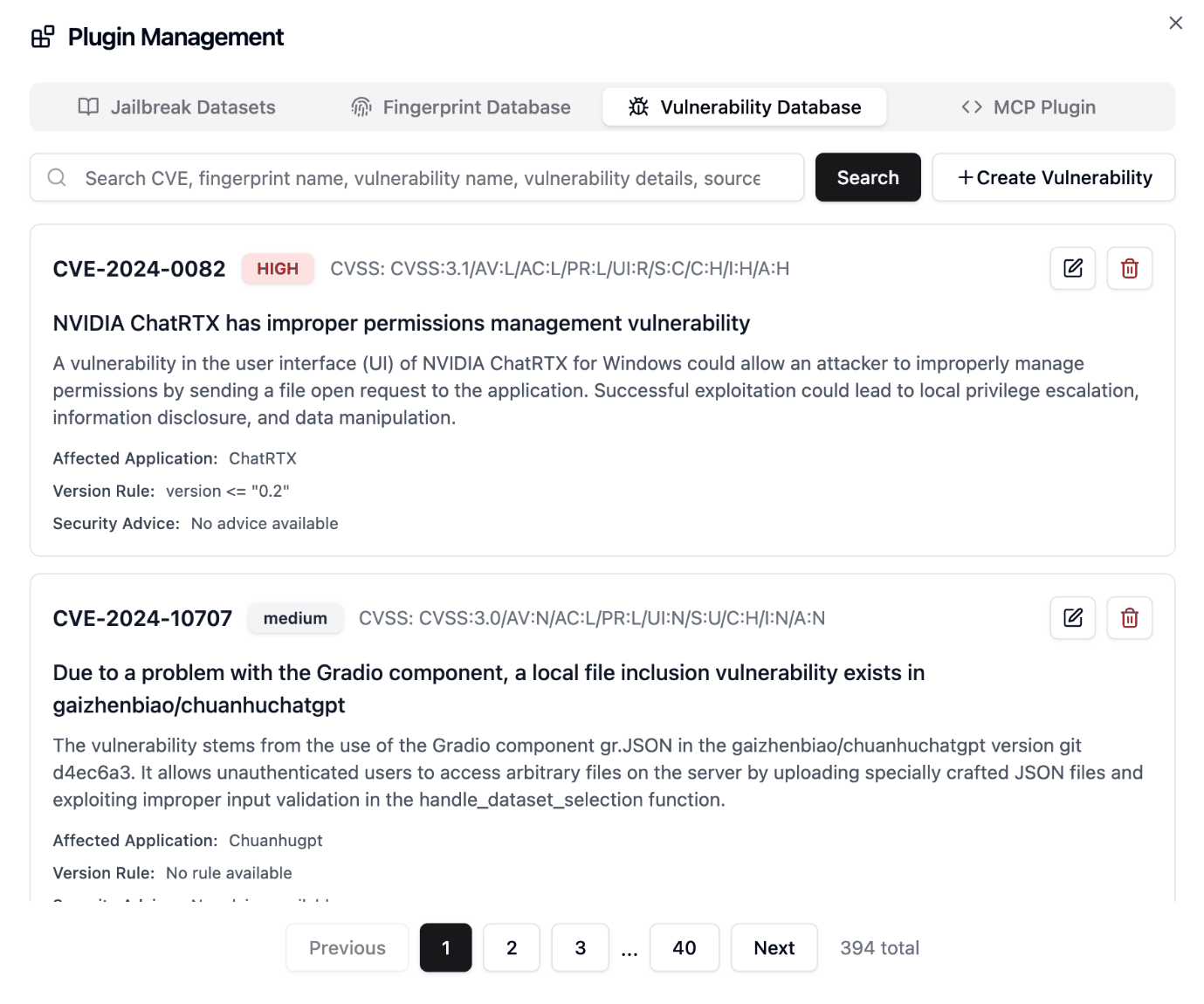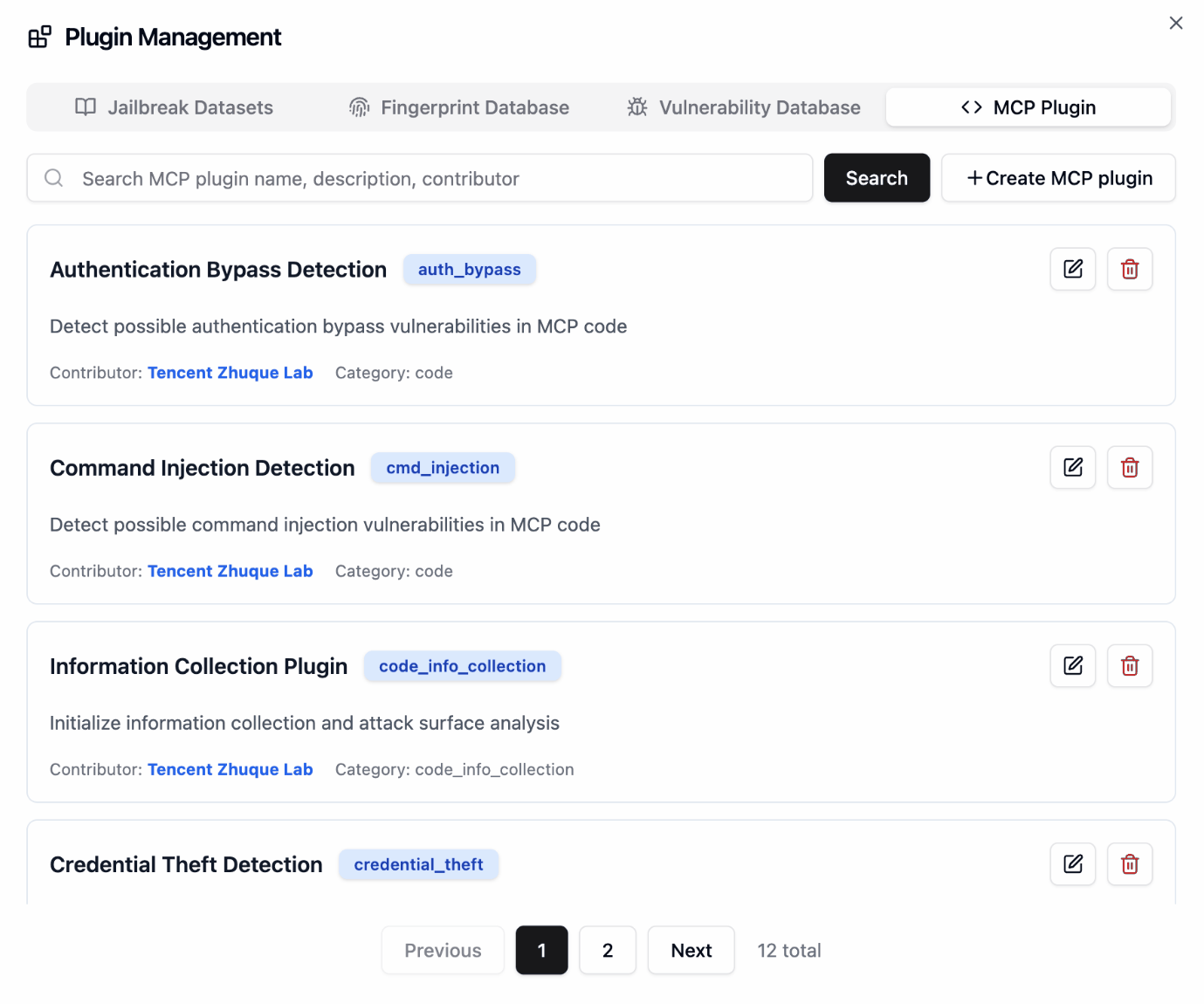
📖 User Guide
Visit our online documentation: https://tencent.github.io/AI-Infra-Guard/
For more detailed FAQs and troubleshooting guides, visit our documentation.
🔧 API Documentation
A.I.G provides a comprehensive set of task creation APIs that support AI infra scan, MCP Server Scan, and Jailbreak Evaluation capabilities.
After the project is running, visit http://localhost:8088/docs/index.html to view the complete API documentation.
For detailed API usage instructions, parameter descriptions, and complete example code, please refer to the Complete API Documentation.
📝 Contribution Guide
The extensible plugin framework serves as A.I.G's architectural cornerstone, inviting community innovation through Plugin and Feature contributions.
Plugin Contribution Rules
1. Fingerprint Rules: Add new YAML fingerprint files to the data/fingerprints/ directory.
2. Vulnerability Rules: Add new vulnerability scan rules to the data/vuln/ directory.
3. MCP Plugins: Add new MCP security scan rules to the data/mcp/ directory.
4. Jailbreak Evaluation Datasets: Add new Jailbreak evaluation datasets to the data/eval directory.
Please refer to the existing rule formats, create new files, and submit them via a Pull Request.
Other Ways to Contribute
🙏 Acknowledgements
🎓 Academic Collaborations
We extend our sincere appreciation to our academic partners for their exceptional research contributions and technical support.
👥 Gratitude to Contributing Developers
Thanks to all the developers who have contributed to the A.I.G project, Your contributions have been instrumental in making A.I.G a more robust and reliable AI Red Team platform.
🤝 Appreciation for Our Users
We are deeply grateful to the following teams and organizations for their trust, and valuable feedback in using A.I.G.
💬 Join the Community
🌐 Online Discussions
- GitHub Discussions: Join our community discussions
- Issues & Bug Reports: Report issues or suggest features
📱 Discussion Community
WeChat Group
Discord
📧 Contact Us
For collaboration inquiries or feedback, please contact us at: zhuque@tencent.com
🔗 Recommended Security Tools
If you are interested in code security, check out A.S.E (AICGSecEval), the industry's first repository-level AI-generated code security evaluation framework open-sourced by the Tencent Wukong Code Security Team.
📖 Citation
If you use A.I.G in your research, please cite:
@misc{Tencent_AI-Infra-Guard_2025,
author={{Tencent Zhuque Lab}},
title={{AI-Infra-Guard: A Comprehensive, Intelligent, and Easy-to-Use AI Red Teaming Platform}},
year={2025},
howpublished={GitHub repository},
url={https://github.com/Tencent/AI-Infra-Guard}
}📚 Related Papers
We are deeply grateful to the research teams who have used A.I.G in their academic work and contributed to advancing AI security research:
[1] Yongjian Guo, Puzhuo Liu, et al. "Systematic Analysis of MCP Security." arXiv preprint arXiv:2508.12538 (2025). [[pdf]](https://arxiv.org/abs/2508.12538)
[2] Zexin Wang, Jingjing Li, et al. "A Survey on AgentOps: Categorization, Challenges, and Future Directions." arXiv preprint arXiv:2508.02121 (2025). [[pdf]](https://arxiv.org/abs/2508.02121)
[3] Yixuan Yang, Daoyuan Wu, Yufan Chen. "MCPSecBench: A Systematic Security Benchmark and Playground for Testing Model Context Protocols." arXiv preprint arXiv:2508.13220 (2025). [[pdf]](https://arxiv.org/abs/2508.13220)
[4] Ping He, Changjiang Li, et al. "Automatic Red Teaming LLM-based Agents with Model Context Protocol Tools." arXiv preprint arXiv:2509.21011 (2025). [[pdf]](https://arxiv.org/abs/2509.21011)
[5] Weibo Zhao, Jiahao Liu, Bonan Ruan et al. "When MCP Servers Attack: Taxonomy, Feasibility, and Mitigation." arXiv preprint arXiv:2509.24272v1 (2025). [[pdf]](http://arxiv.org/abs/2509.24272v1)
[6] Bin Wang, Zexin Liu, Hao Yu et al. "MCPGuard : Automatically Detecting Vulnerabilities in MCP Servers." arXiv preprint arXiv:22510.23673v1 (2025). [[pdf]](http://arxiv.org/abs/2510.23673v1)
[7] Christian Coleman. "Behavioral Detection Methods for Automated MCP Server Vulnerability Assessment." [[pdf]](https://digitalcommons.odu.edu/cgi/viewcontent.cgi?article=1138&context=covacci-undergraduateresearch)
[8] Teofil Bodea, Masanori Misono, Julian Pritzi et al. "Trusted AI Agents in the Cloud." arXiv preprint arXiv:2512.05951v1 (2025). [[pdf]](http://arxiv.org/abs/2512.05951v1)
[9] Yunyi Zhang, Shibo Cui, Baojun Liu et al. "Beyond Jailbreak: Unveiling Risks in LLM Applications Arising from Blurred Capability Boundaries." arXiv preprint arXiv:2511.17874v2 (2025). [[pdf]](http://arxiv.org/abs/2511.17874v2)
📧 If you have used A.I.G in your research or product, or if we have inadvertently missed your publication, we would love to hear from you! Contact us here.
📄 License
This project is licensed under the MIT License. See the License.txt file for details.
Similar MCP
Based on tags & features
Trending MCP
Most active this week